The Best Fluffy Pancakes recipe you will fall in love with. Full of tips and tricks to help you make the best pancakes.
What is a Virtual Private Network?
A virtual private network (VPN) is an internet security service that allows users to access the Internet as though they were connected to a private network. This encrypts Internet communications as well as provides a strong degree of anonymity. Some of the most common reasons people use Virtual Private networks are to protect against snooping on public WiFi; to circumvent Internet censorship, or to connect to a business’s internal network for the purpose of remote work.

How does a Virtual Private Network work?
Ordinarily, most Internet traffic is unencrypted and very public. When a user creates an Internet connection, such as visiting a website in a browser; the user’s device will connect to their Internet Service Provider (ISP), and then the ISP will connect to the Internet to find the appropriate web server to communicate with to fetch the requested website.
Information about the user is exposed in every step of the website request. Since the user’s IP address is exposed throughout the process; the ISP and any other intermediary can keep logs of the user’s browsing habits. Additionally, the data flowing between the user’s device and the webserver is unencrypted. This creates opportunities for malicious actors to spy on the data or perpetrate attacks on the user; such as an on-path attack.

Conversely, a user connecting to the Internet using a Virtual Private Network service has a higher level of security and privacy. A Virtual Private Network connection involves the following 4 steps:
- The Virtual Private Network client* connects to the ISP using an encrypted connection.
- The ISP connects the Virtual Private Network client to the Virtual Private Network server, maintaining the encrypted connection.
- The Virtual Private Network server decrypts the data from the user’s device and then connects to the Internet to access the web server in an unencrypted communication.
- The Virtual Private Network server creates an encrypted connection with the client, known as a ‘VPN tunnel’.
The VPN tunnel between the Virtual Private Network client and VPN server passes through the ISP, but since all the data is encrypted, the ISP cannot see the user’s activity. The VPN server’s communications with the Internet are unencrypted, but the web servers will only log the IP address of the VPN server, which gives them no information about the user.
*The VPN client is the Virtual Private Network software installed on the user’s device.
Is a VPN only for people with something to hide?
As with other Internet privacy services, VPNs are sometimes categorized as tools for illegal or subversive activity. The truth is that there are a number of valid and legitimate reasons to use a Virtual Private Network. Here are a few of the most common:
- Protection over public WiFi – Users who go on public WiFi networks without a Virtual Private Network are putting themselves at risk. Their Internet traffic is unencrypted, and other users on the same network can monitor their activity using easily accessible tools. This is a common way for attackers to steal login credentials and other sensitive information. If a user is connected through a VPN, a snooping attacker will only be able to see encrypted data, which won’t reveal any sensitive information.
- Remote work – Many businesses allow their employees to work remotely using a VPN. This can allow the remote employee to have access to the company’s internal network, as well as provide encryption to protect the business from attackers or spying.
- Freedom from censorship in oppressive states – In some parts of the world, expressing or even reading views that are critical of the government is forbidden. Many of these states also provide their citizens with a suppressed version of the Internet that blocks significant amounts of domains. People accessing the Internet in these states can use a VPN to access content that their state wants blocked, as well as speak freely online, since VPN encryption protects their activity from state surveillance.
- Location anonymity – Some web services will restrict or filter content based on the location of the user. A VPN can be used to anonymize a user’s location and get around these restrictions.
- The right to online privacy – ISPs have been known to sell the private data of their uses. Similarly, some websites will sell information about their visitors. The privacy offered by VPN services enable consumers to opt out of having their data harvested.
What are the downsides of a VPN?
A VPN(Virtual Private Network) service doesn’t guarantee an increased level of security; users can only feel secure with a VPN if they trust the Virtual Private Network provider. A dishonest VPN provider could sell their users’ information or leave them open to attacks. It’s also worth noting that most Virtual Private Network services come at a recurring monthly cost. Some VPN users may also experience issues with performance.
How does a Virtual Private Network affect performance?
Some users will experience performance degradation from a Virtual Private Network, and this depends largely on which VPN service they are using. Not all VPNs are created equal, and if a VPN service does not have the server capacity to handle the load created by their users, those users will experience a slowdown in their Internet connection.
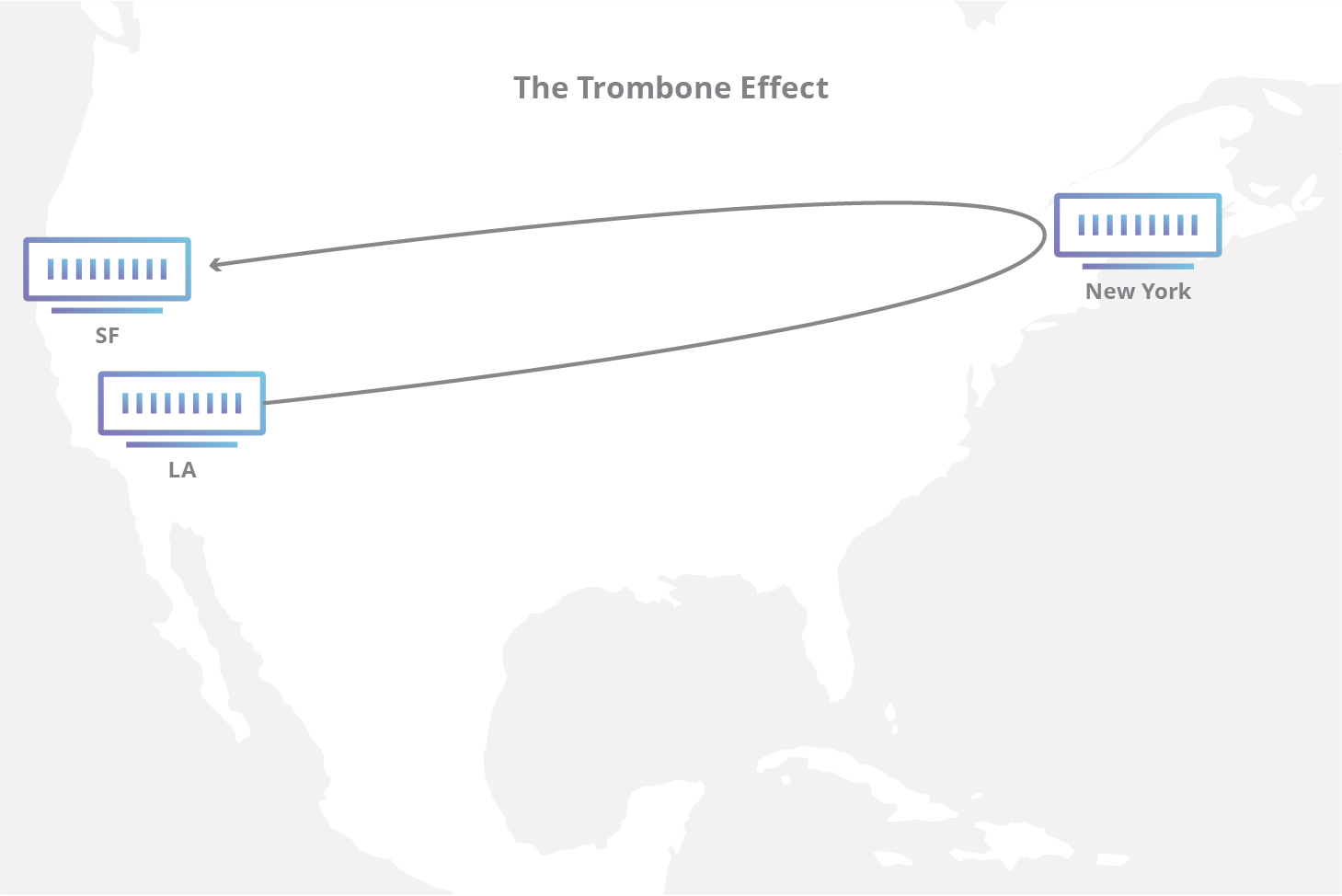
Additionally, if a Virtual Private Network is located a great distance from both the user and the web server they are trying to access, the resulting travel time can create latency. For example, if a user in San Francisco is accessing a web site whose servers are also in San Francisco, but that user’s VPN service is located in Tokyo, the user’s request will have to travel halfway around the world and back before connecting to a server just a few miles away. This is sometimes called the trombone effect.