The Best Fluffy Pancakes recipe you will fall in love with. Full of tips and tricks to help you make the best pancakes.
Parameter tampering is a simple attack targeting the application business logic. This attack takes advantage of the fact that many programmers rely on hidden or fixed fields (such as a hidden tag in a form or a parameter in a URL) as the only security measure for certain operations.
What is Parameter Tampering
Parameter Tampering is a web-based, business logic attack. It involves manipulation of parameters exchanged between client and server to modify the application data such as user credentials, permissions, the number of products etc. It is intended as a business security threat that involves an unauthorized party manipulating and tampering with the website’s URL, web page form or other parameters.
Usually, this information is stored in cookies, hidden form fields, or URL Query Strings, and is used to increase application functionality and control. This attack can be performed by a malicious user who wants to exploit the application for their own benefit, or an attacker who wishes to attack a third-person using a Man-in-the-middle attack. In both cases, tools likes Webscarab and Paros proxy are mostly used.
The attack success depends on integrity and logic validation mechanism errors, and its exploitation can result in other consequences including XSS, SQL Injection file inclusion, and path disclosure attacks.
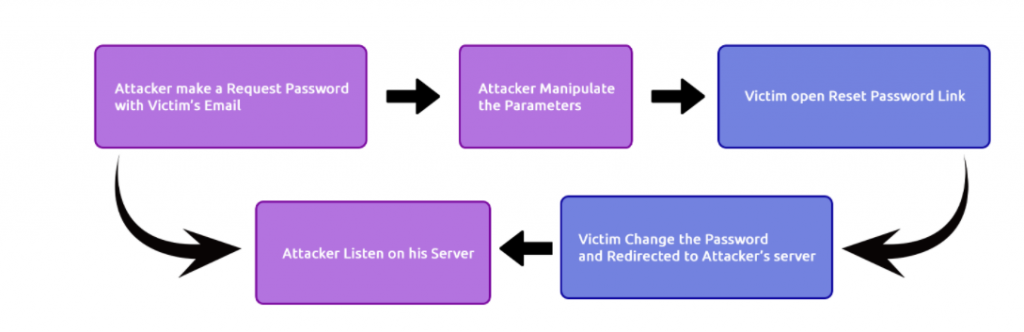
Now Let’s have look on some examples
- Changing a Cheap Product to an Expensive One Scenario: While making a payment, a product is added to a basket on an application. A request is made for the cheaper product and the parameters of the request are saved before the product goes to the bank for approval. Subsequently, a request is made for the expensive product but is replaced with the information about the cheaper product and again sent to the bank for approval. The bank then approves the cheaper product.
- Unlimited Card Scenario: A product that is added to the basket cannot be confirmed by the bank because the balance is insufficient. The “errmsg” parameter in the request, shows the value of “CARD + SALE + LIMIT + INSUFFICIENT” since there is not enough in the user’s credit card balance. However, when the “errmsg”, “response”, and “procreturncode” parameter values in the request are updated, it approves the order.

3. Changing Price Scenario: In this scenario, the price value can be easily changed by lowering the price and passing the order for payments.
While making a payment, a product is added to the basket on the application. In the customer payment request, the price is then edited in the request and sent for bank approval. As seen in the screenshot, the request is intercepted before it is sent to the bank and the “Total Amount” and “Amount” parameters are changed to a different price. The transaction value of the product is changed from “409.98 ” to “0.98” and sent to the bank.
Description
A classic example of parameter tampering is changing parameters in form fields. When a user makes selections on an HTML page, they are usually stored as form field values and sent to the Web application as an HTTP request. These values can be pre-selected (combo box, check box, radio button, etc.), free text or hidden. All of these values can be manipulated by an attacker. In most cases this is as simple as saving the page, editing the HTML and reloading the page in the Web browser.
Hidden fields are parameters invisible to the end user, normally used to provide status information to the Web application. For example, consider a products order form that includes the following hidden field:
<input type="hidden" name="price" value="59.90">
Modifying this hidden field value will cause the Web application to charge according to the new amount.
Combo boxes, check boxes and radio buttons are examples of pre-selected parameters used to transfer information between different pages, while allowing the user to select one of several predefined values. In a parameter tampering attack, an attacker may manipulate these values. For example, consider a form that includes the following combo box:
<FORM METHOD=POST ACTION="xferMoney.asp">
Source Account: <SELECT NAME="SrcAcc">
<OPTION VALUE="123456789">******789</OPTION>
<OPTION VALUE="868686868">******868</OPTION></SELECT>
<BR>Amount: <INPUT NAME="Amount" SIZE=20>
<BR>Destination Account: <INPUT NAME="DestAcc" SIZE=40>
<BR><INPUT TYPE=SUBMIT> <INPUT TYPE=RESET>
</FORM>
An attacker may bypass the need to choose between only two accounts by adding another account into the HTML page source code. The new combo box is displayed in the Web browser and the attacker can choose the new account.
HTML forms submit their results using one of two methods: GET or POST. If the method is GET, all form parameters and their values will appear in the query string of the next URL the user sees. An attacker may tamper with this query string. For example, consider a Web page that allows an authenticated user to select one of his/her accounts from a combo box and debit the account with a fixed unit amount. When the submit button is pressed in the Web browser, the following URL is requested:
http://www.mydomain.com/example.asp?accountnumber=12345&debitamount=1
An attacker may change the URL parameters (accountnumber and debitamount) in order to debit another account:
http://www.mydomain.com/example.asp?accountnumber=67891&creditamount=9999
There are other URL parameters that an attacker can modify, including attribute parameters and internal modules. Attribute parameters are unique parameters that characterize the behavior of the uploading page. For example, consider a content-sharing Web application that enables the content creator to modify content, while other users can only view content. The Web server checks whether the user that is accessing an entry is the author or not (usually by cookie). An ordinary user will request the following link:
http://www.mydomain.com/getpage.asp?id=77492&mode=readonly
An attacker can modify the mode parameter to read write in order to gain authoring permissions for the content.
https://thecyberdelta.com/know-what-is-nmap-network-mapper/

