The Best Fluffy Pancakes recipe you will fall in love with. Full of tips and tricks to help you make the best pancakes.
Cross site scripting is a type of vulnerability that can be found in some web applications. XSS attacks enable attackers to inject client side script in to web pages viewed by other users. A cross site scripting vulnerability may be used by attackers to bypass access control such as same-origin policy.
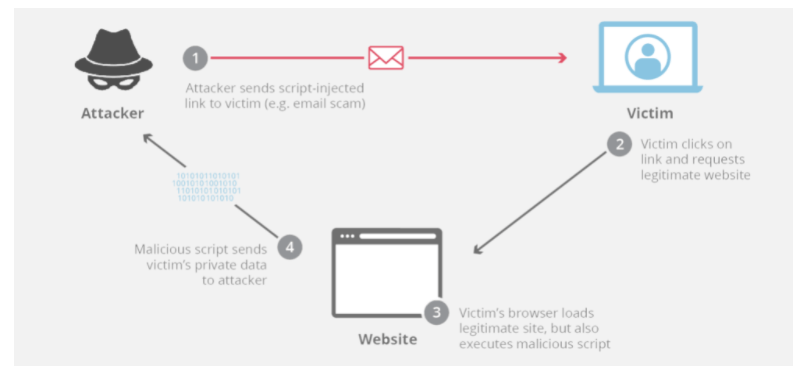
What is cross site scripting
This attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.
An attacker can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. These scripts can even rewrite the content of the HTML page.
Example of cross site scripting
One useful example of cross-site scripting attacks is commonly seen on websites that have unvalidated comment forums. In this case, an attacker will post a comment consisting of executable code wrapped in ‘<script></script>’ tags. These tags tell a web browser to interpret everything between the tags as JavaScript code. Once that comment is on the page, when any other user loads that website, the malicious code between the script tags will be executed by their web browser, and they will become a victim of the attack.
How cross site scripting is use to cause harm

JavaScript cross-site scripting attacks are popular because JavaScript has access to some sensitive data that can be used for identity theft and other malicious purposes. For example, JavaScript has access to cookies*, and an attacker could use an XSS attack to steal a user’s cookies and impersonate them online. JavaScript can also create HTTP requests, which can be used to send data (such as stolen cookies) back to the attacker. Additionally, client-side JavaScript can also help an attacker gain access to APIs that contain geolocation coordinates, webcam data, and other sensitive information.
- The victim loads a webpage and the malicious code copies the user’s cookies
- The code then sends an HTTP request to an attacker’s webserver with the stolen cookies in the body of the request.
- The attacker can then use those cookies to impersonate the user on that website for the purpose of a social engineering attack or even to access bank account numbers or other sensitive data.
Types of cross site scripting attacks
There are three main types of XSS attacks. These are:
- Reflected XSS, where the malicious script comes from the current HTTP request.
- Stored XSS, where the malicious script comes from the website’s database.
- DOM-based XSS, where the vulnerability exists in client-side code rather than server-side code.
How to prevent cross site scripting(XSS)
There is no single strategy for mitigating cross-site scripting, and different types of web applications require different levels of protection. A number of protective measures can be taken are followed as:
If possible, avoiding HTML in inputs – One very effective way to avoid persistent cross-site scripting attacks is to prevent users from posting HTML into form inputs. There are other options which let users create rich content without the use of HTML, such as markdown and WYSIWYG editors.
Validating inputs – Validation means implementing rules that prevent a user from posting data into a form that doesn’t meet certain criteria. For example, an input that asks for the user’s “Last Name” should have validation rules that only let the user submit data consisting of alphanumeric characters. Validation rules can also be set to reject any tags or characters commonly used in cross-site scripting, such as “<script>” tags.
Sanitizing data – Sanitizing data is similar to validation, but it happens after the data has already been posted to the web server, yet still before it is displayed to another user. There are several online tools that can sanitize HTML and filter out any malicious code injections.
Taking cookie security measures – Web applications can also set special rules for their cookie handling that can mitigate cookie-theft via cross-site scripting attacks. Cookies can be tied to particular IP addresses so that cross-site scripting attackers cannot access them. Additionally, rules can be created to block JavaScript from accessing cookies altogether.
https://thecyberdelta.com/pegasus/
https://thecyberdelta.com/how-to-find-if-a-link-has-an-ip-address-tracker/

